Two-factor authentication (2FA) is a crucial security measure that protects your account from malicious login attempts. In this article, we will briefly explain the fundamentals of 2FA and how it integrates with YouTestMe GetCertified.
Activating the 2FA on My profile page
To activate the 2FA authentication, navigate to the My profile page and select the Activate two-factor authentication button.
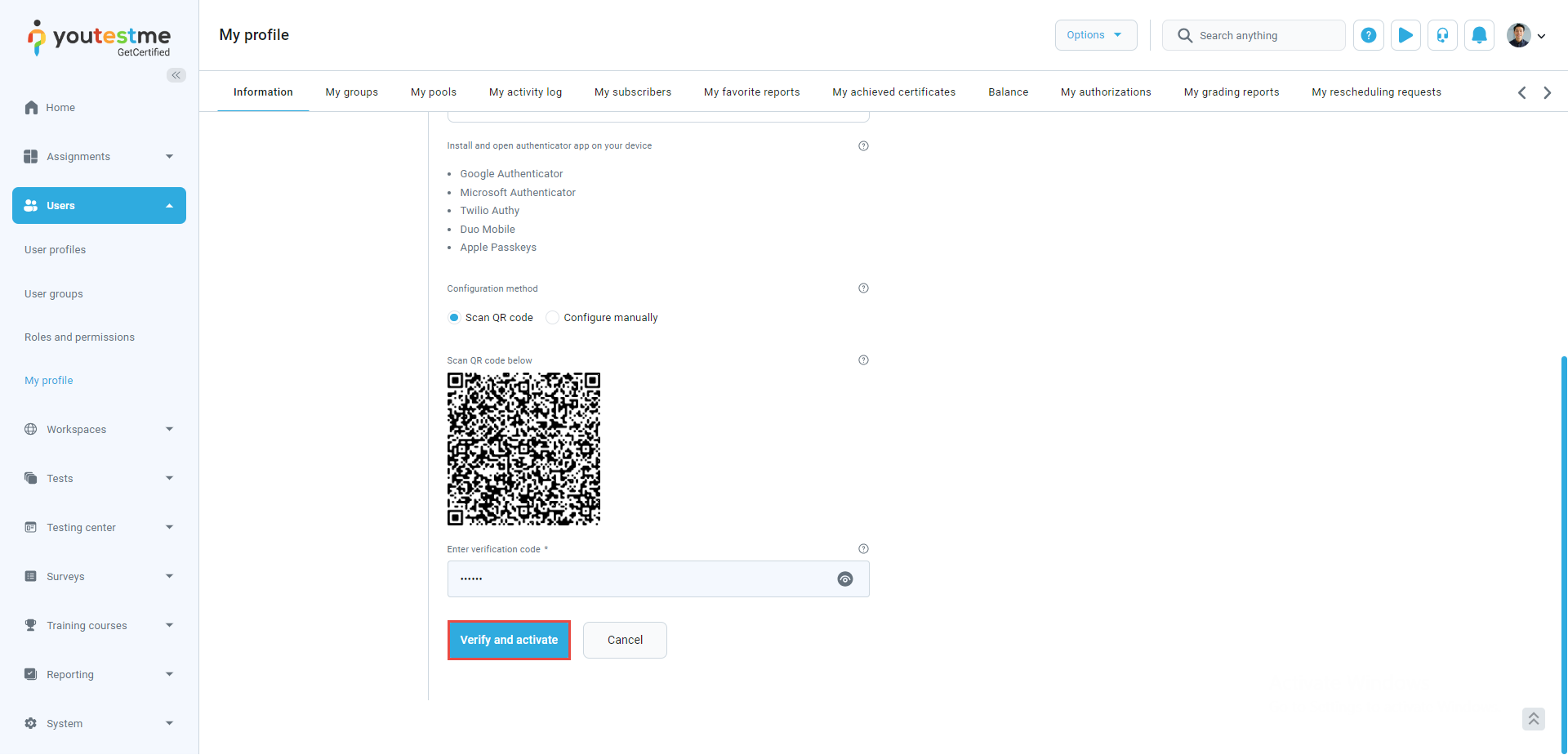
You need to install one of the authentication apps on your device. Moreover, you will need to scan the QR code with the application. You are provided with the list of the most popular authentication apps. The app is suitable for mobile phones.
Scanning the QR code
You can set up custom two-factor authentication settings:
- The hash algorithm for generating one-time verification codes — The adept user can fine-tune the hash algorithm according to the specific security protocols they deem most effective. Standard options include SHA-256, SHA-3, or the more traditional MD5.
- The lifetime of seconds of the single verification code — This numerical value, measured in seconds, determines how long each code remains valid. Tailoring this setting allows you to strike a balance between security and convenience.
- The length of the generated verification codes — Adjust this value to align with your security posture. A longer code offers increased complexity, making it more resistant to malicious attempts at deciphering.
Note: The QR code changes after any setting change, and these settings must be the same on the authenticator app.
After scanning the QR code, you will get the code through your authentication app. Enter the code in the appropriate field and select the Verify and activate button.
Users can enable and disable the two-factor authentication, but the admin accounts possess the authority to disable it. This is particularly useful in scenarios where a user loses the device linked to the receipt of verification codes.
After trying to log in with the user with the two-face authentication set, the application will request the verification code sent to the user’s device.
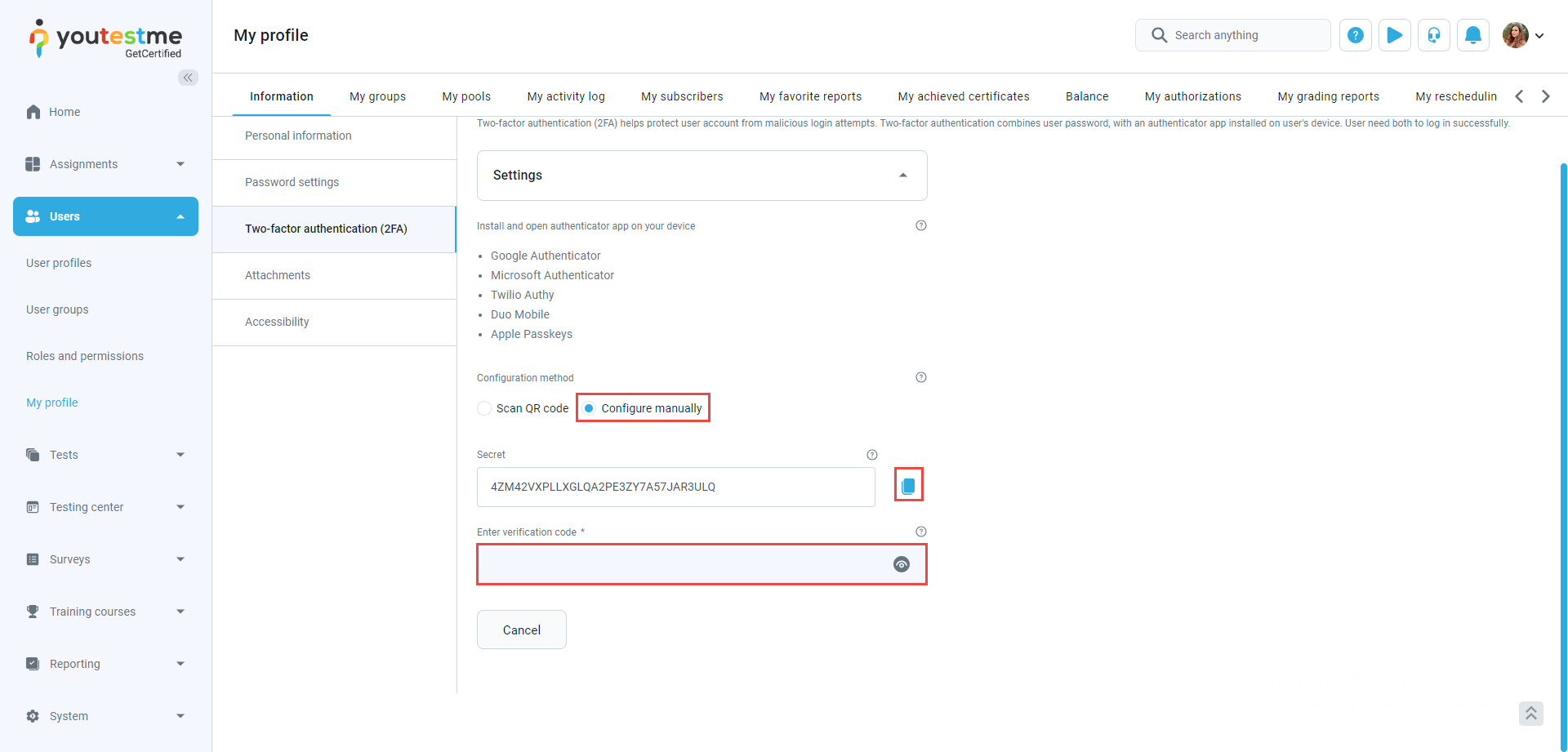
Manual configuration
An additional method for setting up two-factor authentication entails a manual configuration process. Users input the provided secret key directly into their authentication app in this approach. Following this step, the user will receive a verification code to enter into the designated field to complete the setup.
How 2FA Works — A Simple Explanation
In today’s digital world, keeping your online accounts secure is essential. Two-factor authentication (2FA) is a key tool in achieving this. Let’s break it down into two easy steps:
- Step 1 – Something You Know: Start by entering your username, something you already know, to access your account.
- Step 2 – Something You Have: After entering that information, you are prompted for a verification code. This code is sent to your mobile phone via text message or generated by an authenticator app, such as Google Authenticator. You enter this code to complete the login. This constitutes the second factor, something you have, which is dynamic and can constantly change.
By requiring both the static knowledge of the first factor and the dynamic, time-sensitive code (the second factor), 2FA adds an extra layer of security. Even if someone were to obtain your login credentials, they would still need access to your phone or authenticator app to log in successfully.
Multifactor Authentication at the SSO Level
In another scenario, when you’re logging into YouTestMe using Single Sign-On (SSO), things work a bit differently. You’ll need Multi-Factor Authentication (MFA) if you’re not logged in through SSO. To better understand SSO, check this article example where we used integration with Okta.
When initiating an SSO login and the user does not already have an active SSO session, MFA becomes mandatory to access the identity provider, ensuring an added layer of security and authentication.
Explaining 2FA with an Authenticator Application
When implementing 2FA using an authenticator application, the process typically includes user registration, generating a secure time-based one-time password (TOTP) secret key, and providing an easier setup using QR codes. Users are instructed to download an authenticator application on their mobile device, such as Google Authenticator or Microsoft Authenticator. This application allows them to scan QR codes provided during registration. Before displaying QR codes, the secret keys associated with user accounts are securely stored in the application’s backend.
After setup, users are prompted to enter verification codes generated by the app, which are time-based one-time passwords (TOTPs) derived from their secret keys. Successful verification enables 2FA for their accounts or grants access to the application.
In addition to these steps, providing users with a set of backup codes during the registration process is considered good practice, serving as an alternative verification method in case they lose access to their authenticator application. Ensuring a smooth user experience involves error handling, offering clear instructions, and addressing potential issues during the authenticator application setup.
Lastly, users should be educated on the importance of securing their authenticator applications and backing up their recovery codes.